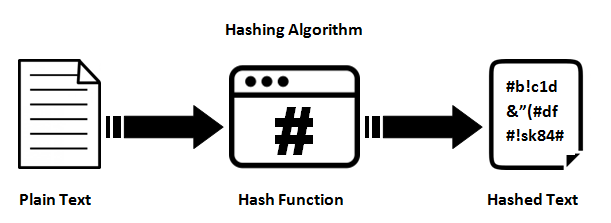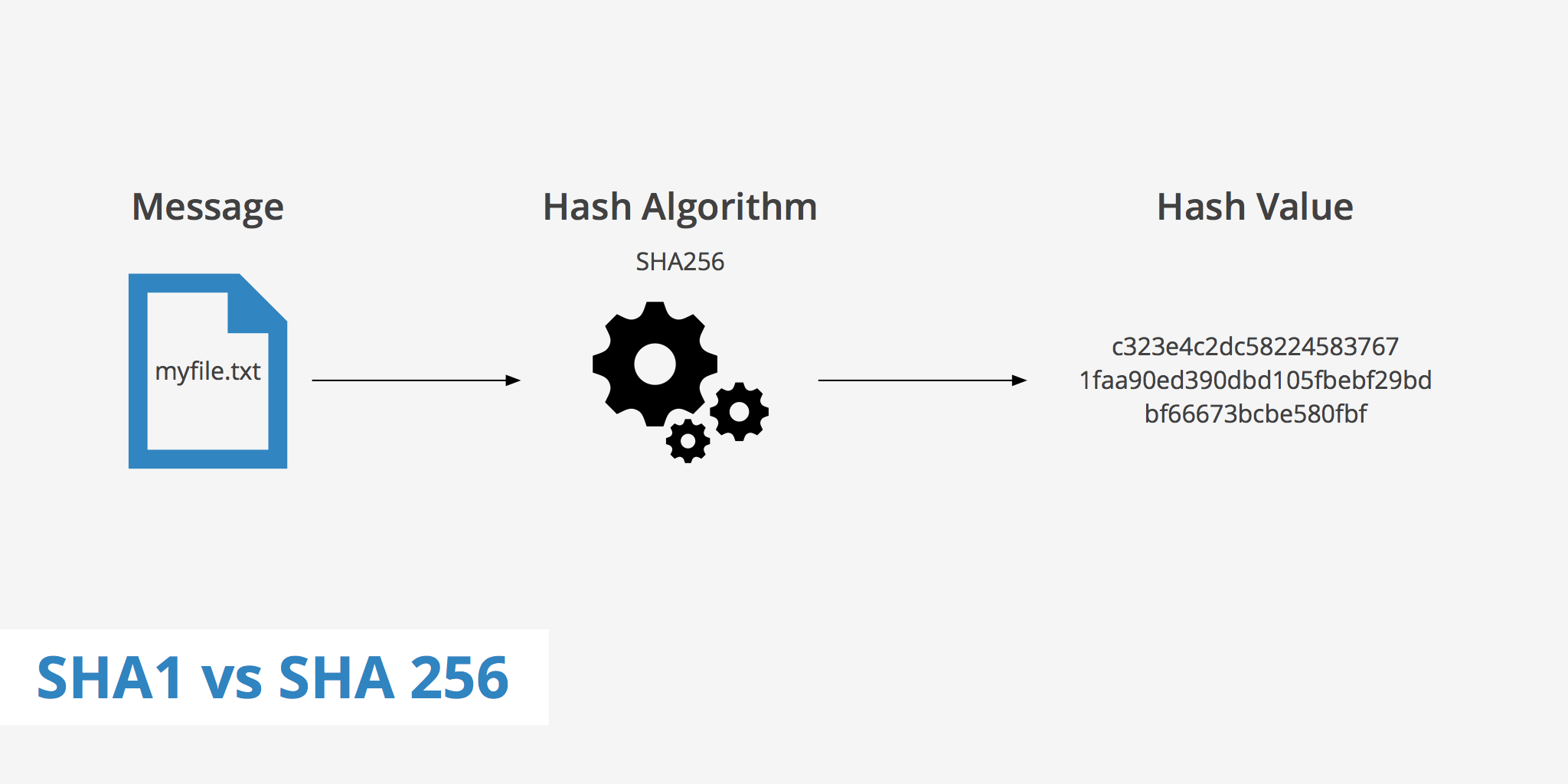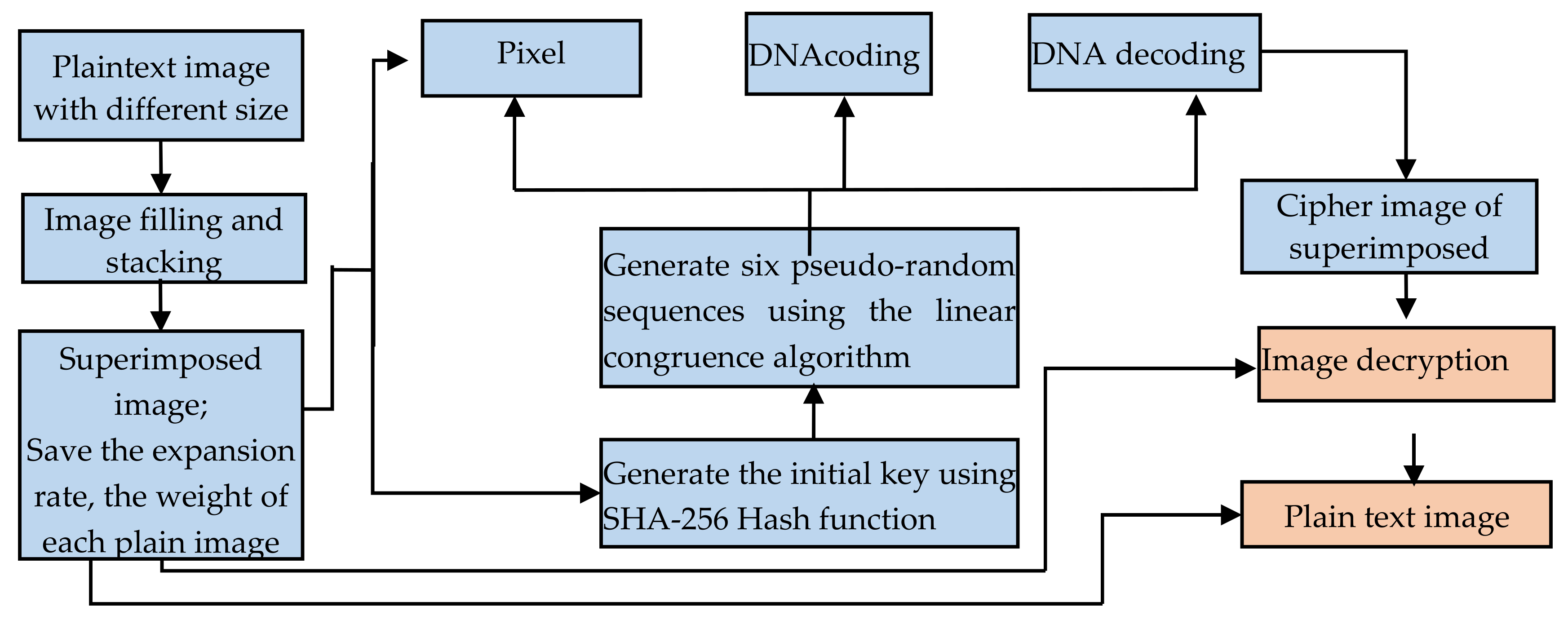
Entropy | Free Full-Text | A Multiple-Medical-Image Encryption Method Based on SHA-256 and DNA Encoding

Multimedia stream hashing: A forensic method for content verification - Wales - 2023 - Journal of Forensic Sciences - Wiley Online Library